Here is how I defeated the Tr0ll challenge, if you wish to have a go at this yourself you can download it from here.
SPOILER ALERT – If you don’t want to find out how to defeat the tr0ll then don’t read on.
The Tr0ll VM has a DHCP server set up so should automatically be assigned an address on the network, so let’s begin by scanning the network for the host.
root@kali:~# nmap -sn 192.168.0.*
Figure 1 – Host scan

nmap host scan
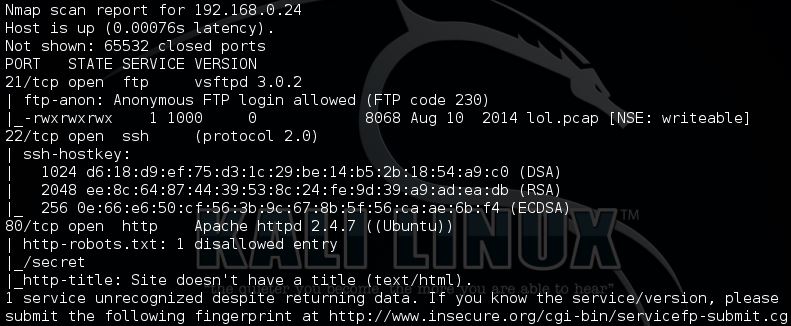
Now we know the address of the vulnerable VM we can do a full TCP Nmap scan of the host.
root@kali:~# nmap -sS -p- -Pn -A 192.168.0.24
Figure 2 – Full TCP scan on all ports with additional information gathering scripts
There are a few interesting points that the TCP scan has picked up, however before doing that we will first check for open UDP ports.
root@kali:~# nmap -sU -Pn -T5 192.168.0.24
The UDP scan revealed no results, so on to looking at the TCP results in figure 2.
Let’s start by looking at what’s running on port 80 (http) – as you can see from figure 3 below we’re already being taunted by the troll!
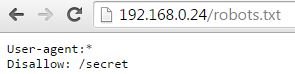
In the port scan results there are a few interesting directories too, let’s start by looking at the robots.txt file for the disallowed entry.
As you can see the /secret directory is disallowed, let’s check it out
Oh No, we’ve been trolled again!.
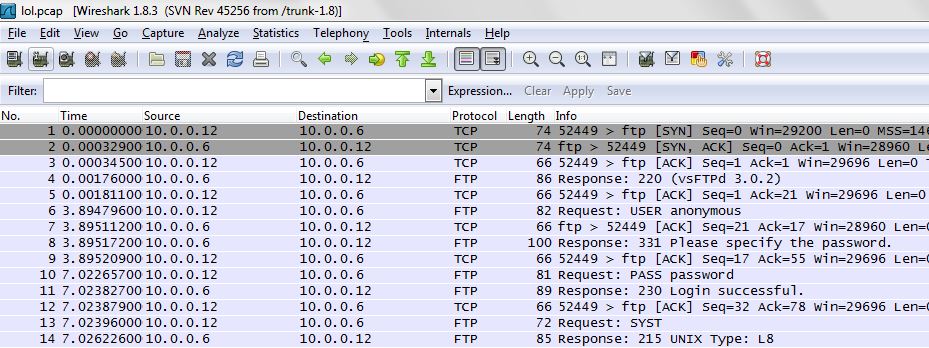
Let’s move on to the FTP server, if you recall it allowed anonymous read access which gave us a file called lol.pcap as shown below:

pcap file on FTP server
Let’s check it out and open it with Wireshark
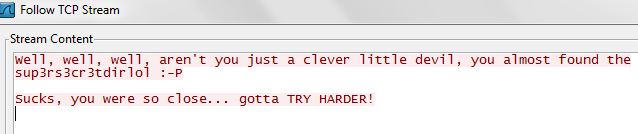
from the initial look the Wireshark capture file is showing the anonymous login over FTP. A closer look at some of the other packets revealed some interesting information when looking at line 42 and following the TCP stream.
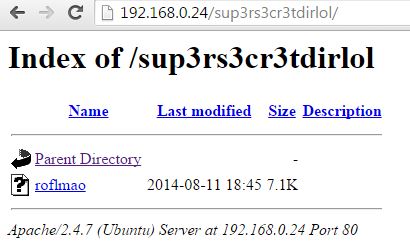
Hmmmmm interesting!, I wonder if that is a directory on the web server?.
BOOM!, now we’re onto something good.
We can now download the file called roflmao, and then open it within a text editor

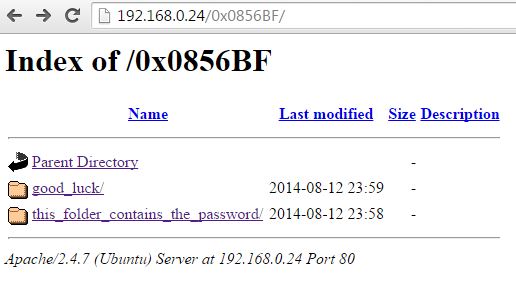
0x0856BF address
There is an interesting memory address which appears as a string within the notepad file. I wonder if it is also a directory name too?.
Bingo!, we are now presented with two different directories. Let’s look at the first one called good luck

usernames directory
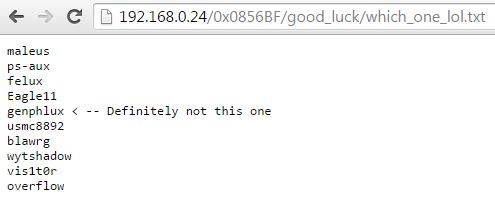
What’s this text file?
I am pretty sure that this is a list of usernames that we could use to login to SSH, additionally normally when I am presented with something like this in a challenge I will start from the bottom of the list and work my way up. So let’s start with overflow as the username.
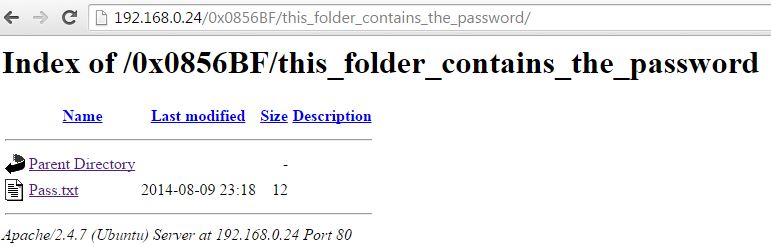
Let’s check out what’s inside the other directory.
Let’s check out this Pass.txt file.

good job password
Let’s try it over SSH.

incorrect SSH password
Hmmm password is incorrect, I still have a feeling that we’re being trolled. at a closer look at the password directory below it says “this folder contains the password”.. What if the file name was actually the password.
Let’s try the file name instead with our username.

successful SSH connection
BOOM!, WE’RE IN!. The next stage of this hacking challenge is to root the box.
STAY TUNED AND I WILL ADD THIS TO THE TUTORIAL IN THE NEXT FEW DAYS


3 comments
Hello, i have a question about your Keylogger post: how can i keep all files in the log txt from overwriting itself?
Wow, that was mindblowing haha but did you finish rooting the box, if so, could you please post it?
Did you finish it?
Comments are closed.